IAM on Google Cloud Platform
What does IAM mean? What are members, roles and policies on Google Cloud Platform? What is resource hierarchy? What are GCP IAM Best Practices? Read on to know more……
What is IAM (Identity Access Management)?
IAM is a framework of policies and processes defined by the Cloud Provider to make sure users have appropriate permissions to access resources, applications and data on the Cloud. This helps not only secure the data and prevent unwanted threats, but also makes sure all the users have the right amount of access to get their work done.
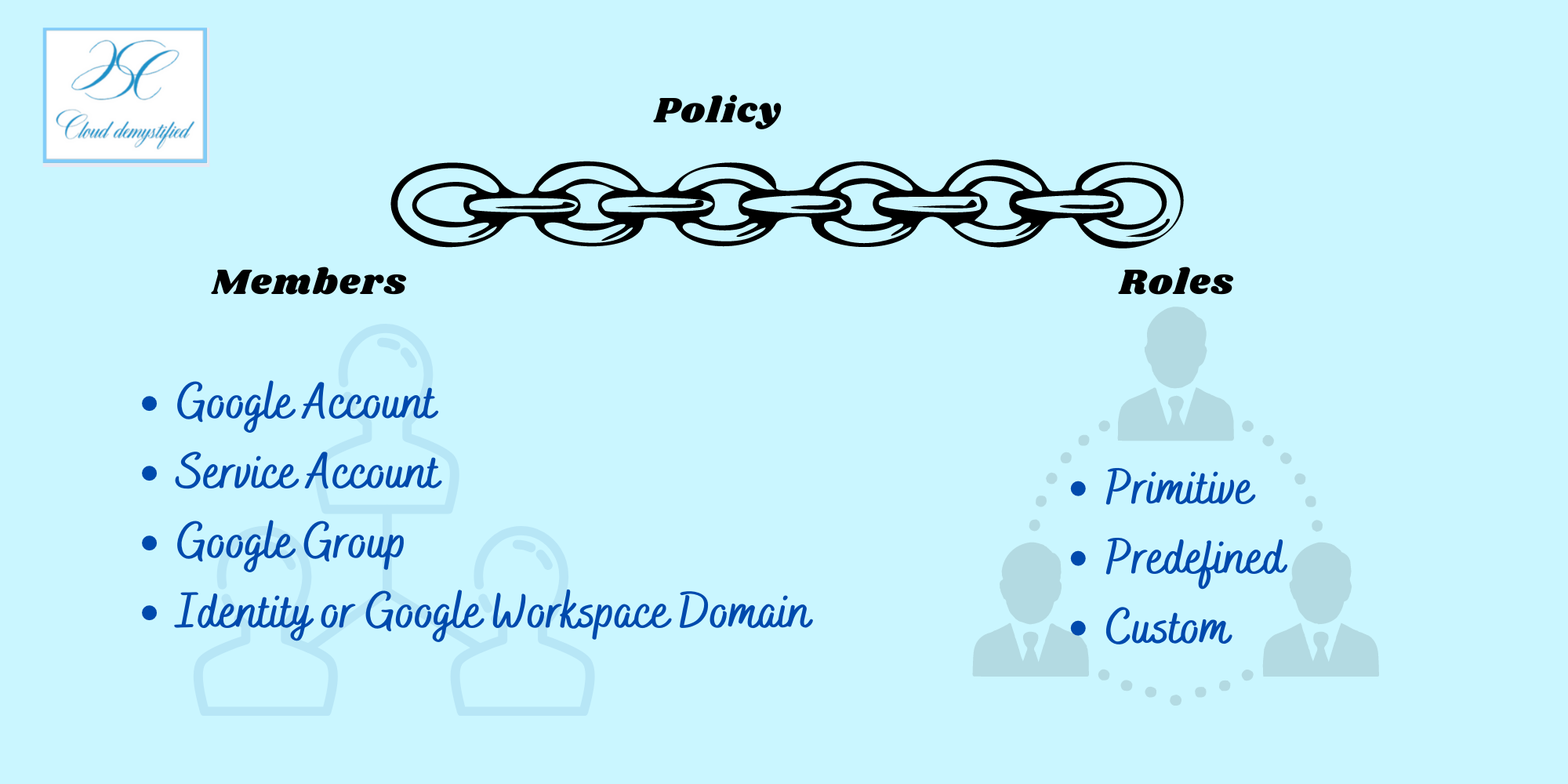
There are three main parts to Identity Access Management (IAM) in Google Cloud Platform (GCP). They are Members, Roles and Policies.
Member
Members are users who need access to resources, applications and/or data on Google Cloud Platform. A member can be a Google account for an end user, a service account for applications and virtual machines, a Cloud Identity domain, or Google Group. Every member has an identity attached to them, which is the “who” part of IAM. This identity can be in the form of e-mail addresses for Google accounts or a domain name associated with Workspace or Cloud Identity domains.
Role
Roles are simply a collection of permissions given to members to access resources, applications, or data on the Cloud. Whenever we assign a role to a member, they get all the permissions associated with that role. For example, when you assign the editor role to someone for your Google document, they receive permission to edit the document. There are three types of roles in Google Cloud Platform. Primitive, Predefined and Custom Roles.
Primitive Roles
Primitive roles consist of the three basic roles of owner, editor and viewer. Since these roles are very broad and not fine-grained, Google Cloud Platform has come up with Predefined and Custom roles for better access control.
Predefined Roles
Predefined roles are more fine-grained, granular roles that Google has defined based on common use cases. These roles provide members with specific access to services and are completely managed by Google Cloud. For example, roles/appengine.appCreator gives members permissions to create an app on App Engine. This is more fine grained than providing them editor access to the entire folder. Google has a big repository of all the predefined roles with their descriptions and permissions.
Custom Roles
Custom roles are fine-grained, granular roles specified or created by the user to provide specific access to members on Google Cloud Platform. These roles are created only if Google doesn’t have them predefined already, and are managed by the user. Custom roles define permissions in the format of service.resource.verb. For example, compute.instances.delete lets the members delete instances on Compute Engine.
Custom roles include a launch stage, which needs to be managed by the users. These stages are ALPHA, BETA and GA, which lets the users track when the roles are available for launch and use. It’s the responsibility of the users to keep these roles updated, since they’re not managed by Google Cloud.
Policy
Policies bind one or more members to a role, and define who has what type of access on Google Cloud. For example, you can set a policy for all users belonging to the HR and Finance division of the company to delete Pub/Sub topics. The following Infographic shows how these three pieces get tied together.
Resource Hierarchy
All Resources on Google Cloud Platform are organized hierarchically. They are grouped into 4 parts- Organization, Folders, Projects and Resources. Organization, for example a company that is using Google Cloud is the top node followed by Folder, Project and Resources. Each resource has only one parent, i.e. Compute Engine, App Engine etc. can only have one Project as a parent.
Children inherit the policies of their parents, i.e. the policies set for the parents are inherited by the child nodes. For example, policies set for a particular Folder are inherited by the Projects under it. For this reason, policies set at the Organization node are inherited by all the Folders, Projects and Resources under that Organization by default.
Let’s understand this with an example. Once Cloud Demystified grows, we’ll need a team of writers, illustrators, etc., who in turn will be given projects to work on, that are hosted on certain applications or systems running on Google Cloud.
Here, Cloud Demystified is the Organization, and the various teams (Writers, Illustrators, Marketing) are grouped under Folders. Each of these teams is given different projects to work on, and we’ll assign Comic1 and Doodle1 assigned to the Illustrators. These projects run on a resource, and we’ll run Comic1 on Cloud Pub/Sub for the purpose of this example. Any policies assigned to Cloud Demystified, like the ability to view all files on a particular Virtual Machine are automatically assigned to all the Folders, Projects, and Resources. Similarly, any policies assigned to the team of Illustrators are inherited by Projects Comic1 and Doodle1 which are then inherited by Topic 1 on Cloud Pub/Sub. In case we specify a different policy for Comic1 or Doodle1, that policy overrides the policy inherited by those projects from the Illustrator Folder. For example, if we want to give Members in Project Comic1 only the viewer role to a particular Virtual Machine, it wouldn’t matter what policy we set for the Organization Cloud Demystified. Members of Comic1 will only have viewer access and will override any policies set at the parent or Organization node.
Think about this like your heredity. You inherit from your larger ethnicity, i.e. Asian, European, African, American etc. You’ll inherit the color and features from your ethnic background or your parents by default, but it’s possible that you can have a different color or features after birth.
Best Practices
The following infographic highlights some of the best practices suggested by Google Cloud for Identity Access Management
Additional Resources
Google Cloud IAM Documentation- https://cloud.google.com/iam/docs/overview
Cloud IAM on Qwiklabs- https://www.qwiklabs.com/focuses/551?parent=catalog
Identity and Access Management (Coursera)-https://www.coursera.org/lecture/gcp-fundamentals/identity-and-access-management-iam-1zsAc